Security in the New Normal – AWA
- Are my documents secure from being copied
- Are my credentials (password/user name) secure from being copied
- Are my online actions secure from being tracked?
- Are my personal details secure from being revealed by sites I visit.
When your star wants to kill a hit TV series
Disney tries to walk the fine line of not acquire the animosity of political groups as much as they can and that has served them well overall. And for that reason, I figure Mouse Country HQ is not very happy with this stupidity.
Your star actor behaves like a little bitch of the Empire and threatens a hit show, ain’t that a kick in the balls? Politicizing Star Wars was not a wise decision. Not even Mof Gideon is that stupid.
PS: Somebody pointed in Facebook that The Mandalorian can be replaced since he keeps the helmet on 95% of the times. As for the 2 first seasons? There is always DeepFake
The storming of the Capitol is the Democrat’s Reichstag fire
That is not an understatement.
Congressman Hank Johnson said on MSNBC, to the man that incited the Crown Height pogrom riots, that the storming of the Capitol was a race war and he and others would have been lynched.
.@TheRevAl @MSNBC The nation, GA & South have made a lot of progress but the attempted coup showed how far we still have to go and how white supremacy still rules the day in America. pic.twitter.com/gHno4UE1qV
— Rep. Hank Johnson (@RepHankJohnson) January 9, 2021
Congresswoman Alexandria Ocasio-Cortez told ABC that half of Congress was about to be murdered.
https://twitter.com/Breaking911/status/1348379468834996226
“And so, if we allow insurrection against the United States with impunity, with no accountability, we are inviting it to happen again,” Ocasio-Cortez said on ABC’s This Week with George Stephanopoulos. “We came close to nearly half of the House dying on Wednesday.”
The media has latched onto the word insurrection. A word not used to describe the annexation of territory by the CHAZ/CHOP or other autonomous zones created by Antifa, or the continuous seige of the Portland Federal Courthouse.
As I mentioned before, Congresswoman Cori Bush drafted a resolution to expel 138 Republican members of the House who challenged the certification of the Electoral College votes.
I believe the Republican members of Congress who have incited this domestic terror attack through their attempts to overturn the election must face consequences. They have broken their sacred Oath of Office.
I will be introducing a resolution calling for their expulsion. pic.twitter.com/JMTlQ4IfnR
— Congresswoman Cori Bush (@RepCori) January 6, 2021
Senators Ted Cruz and John Hawley are being told to resign, with the accusation that their legal challenge incited an insurrection.
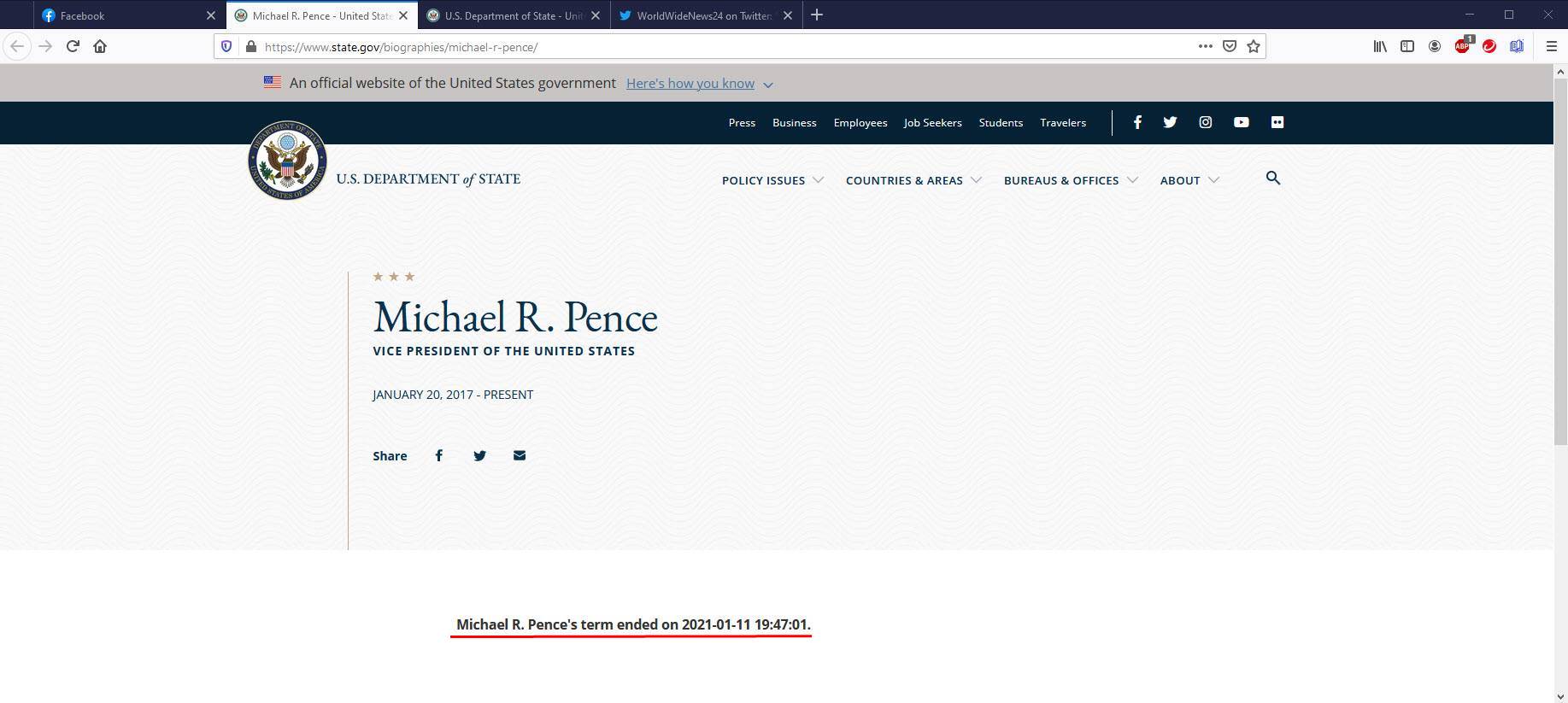
Pelosi announced she will impeach Trump again if Pence doesn’t have him removed by the 25th Amendment.
Biden himself called these people “domestic terrorists.”
We are watching in real time as social media and Big Tech is colluding in violation of every anti-trust law to kick Right Wing voices off the internet.
The Democrats are claiming that they could have been massacred to justify the largest crackdown on Americans since another Democrat signed Executive Order 9066.
When Senator Chuck Schumer said the the storming of the Capitol was like Pearl Harbor, he wasn’t lying.
Sen. Schumer compares today's events to Pearl Harbor:
"Franklin Roosevelt set a day aside that will live in infamy. Unfortunately, we can now add January 6, 2021 to that very short list of dates in American history that will live forever in infamy." pic.twitter.com/mVMrVbuxQ8
— Daily Caller (@DailyCaller) January 7, 2021
We called it absurd to compare a riot to military attack that killed 2,335 Americans. He meant in terms of the restrictions on civil liberties that was going to happen to the ground identified as the enemy.
They are going to push this to the breaking point in their crackdown on the Right.
What happened to Second City Blog?
Suddenly it is locked down, invitation only?
They have been a brutal spike on the Chicago PD’s White Shirts and the administration of Mayor Lori (Beetlejuice) Lightfoot. I would not be surprised if something was forced upon them in this Era of The Purge.

Hat Tip Royko