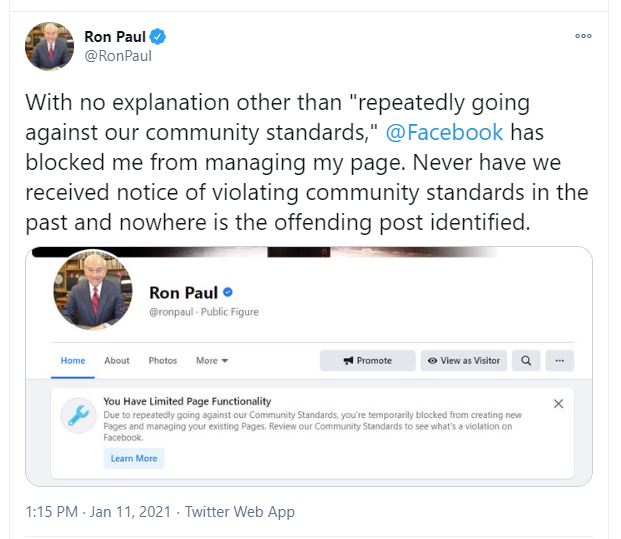
Miguel asked me to write up something about using VPNs. I’ve chosen to make it a bit broader.
The first thing to know about Internet security is that the Internet was not designed to be secure. It was designed to share information.
If you are a person that is interested in security, you are interested in a number of different moving parts.
- Are my documents secure from being copied
- Are my credentials (password/user name) secure from being copied
- Are my online actions secure from being tracked?
- Are my personal details secure from being revealed by sites I visit.
As designed, sending packets (smallest data block that gets transmitted on the net) are open. Anybody that can intercept that packet can read what is in that packet. Thus if you sent an email in 1990 time frame that said “The Libian’s are going to attack the power plant at 1837 on Nov 1st” anybody that was monitoring the network could read that.
The internet is built on a store and forward. So each packet moves from one “computer” to the next. At the next computer, the computer decides where to forward that packet to. Today we have specialized computers called switches and routers to do this store and forward.
There is NOTHING to keep somebody from programming a router/switch on a network to forward all packets to a collection point.
The point of all of this is that everything sent over the net can be monitored and read.
We, the internet geeks started to fix this. The first step was to protect particular types of communications. So instead of sending our passwords and usernames on post cards (Packets) we did some math magic and exchanged magic tokens that could be copied but were useless to the person that copied them.
We created methods of encrypting documents and email. But for the most part, it just didn’t work very well.
The biggest problem is that most users don’t have a clue how to manage secure information. To often people use a password that is easy to guess or that they write down or a dozen other things. They keep copies of secured documents in decrypted form. All of which is bad.
So we created a new protocol for communicating which is called “end to end encryption” What this means is that a data entity is encrypted before it goes on the net (wire) and can only be decrypted at the remote end. The protocol we use for this at a user level is called “ssh”. It was written by some very smart people that understood cryptography and there have been few security issues with it.
For the rest of the people, we got SSL. This is the protocol used in web browsers and to fetch your email and a bunch of other things. You see it if you have the lock in your browser window or you see “https” in a URL.
So now we have secure communications between us and somebody else on the net. Good.
But what does this actually provide us? Not enough. The bad guy/government agent watching your internet traffic might not know exactly what you are viewing, but they will know what websites you are visiting. So they can see that you are watching that porn video of two guys in rabbit suits doing… but they do know you were visiting the website where porn is served from. They don’t know what you said or read on
gunfreezone.net, but they do know you are visiting the site.
This article talks about what can be done with that “metadata”, who you are talking to:
A VPN is designed to solve the meta data issue. So what happens is you fire up your computer and turn on your VPN. Now all your traffic leaves from your computer, your office or house or local McDonalds and travels to a server somewhere on the net, all encrypted. The spies don’t know what you said or who you are saying it to.
Once it gets to those servers, it is then sent repackaged and sent on to its destination. The address on the packet not directly associated with you. Now they don’t know what sites you are visiting. Wowsers!
Except you are a stupid git and you log in and check your email while using your VPN. There is now a log entry at your email service provider saying that at 2021-01-11 17:43:04 you pulled email to such and such IP address.
The bad guys, either legally or by other means get that log entry. They now have the IP address you were using from your VPN and can track that IP address coming into
gunfreezone.org. They know you visited GFZ. VPN or not.
So you decide to go full out and install a Tor browser on your computer and use that instead. Except the feds have put a tor server out there. What they do is they watch for packet counts and sizes that match you. As soon as they see that, they can start tracking the traffic back to your physical location.
There was a “dark web” sales site called The Silk Road. Yeah, you could buy *THAT* there. Yes, that too. And that other thing as well. It was a black market selling really black things.
The guy that designed it was really really careful. He had a laptop dedicated to silk road administration. He always used a VPN and Tor protocols. He always connected via a public wifi and never used his own. He was freaking careful. And he was in a hurry one day and checked his email while using his silk road laptop. That was all it took. The feds arrested him shortly there after. They had been tracking him.
Just this last month there was the single biggest transfer of money out of Bitcoin ever. It turns out that the feds, after multiple years, finally got access to the dudes Bitcoin wallet and transferred out over a Billion Dollars in value.
TL;DR; A VPN is a good thing to use. But it isn’t going to help you. It is stupid things that will get you. Did you remember to shut down every single thing that connects to the internet while you were using the VPN? Nope, then there is a record, somewhere, of the VPN being used by *you* to do something normal. And that lets them know you were using that IP address right then.
And even if you do everything right, there is always a chance that somebody you are working with isn’t that careful and they will expose you. Today they are talking about a hack of Parler over the last few days that exposed 70 Terabytes of data and exposed every single piece of information that Perler had.
Be safe out there, everything you say on the Internet is forever and everything you say can, at some point in time, be tracked back to you.
Thanks for reading,
AWA